Family Educational Rights and Privacy Act: Complying with FERPA and Protecting Higher Education Students in Today’s Technology-Driven World
Schools have an obligation to protect the privacy of students and families, but in today’s technology-driven world, it has become a challenge. The Family Educational Rights and Privacy Act (FERPA) outlines how administrators and faculty can secure families’ private information, but increased cyberthreats and cyberattacks have posed a challenge for both K-12 and secondary schools.
As stated on the federal School Safety website, our growing dependence on technology systems – coupled with emerging, evolving and increasingly deceptive cyber threats – demands enhanced awareness and vigilance when it comes to our online world. It is important for schools, parents and students to stay safe online by taking proactive steps to defend against risks and strengthen cyber safety and security both at home and within schools.
What is FERPA?
Signed into federal law by President Ford on August 21, 1974, the Family Educational Rights and Privacy Act (FERPA) affords parents the right to have access to their children’s education records, the right to seek to have the records amended and the right to have some control over the disclosure of personally identifiable information (PII) from the education records.
Under FERPA, a school generally may not disclose PII from a student’s education records to a third party without prior written consent, with several exceptions. Those exceptions include such things as school officials’ access to the records, the creation of directories and for school enrollment purposes.
When a student reaches 18 years of age or attends an institution of postsecondary education at any age, he or she becomes an “eligible student,” and all rights under FERPA transfer from the parent to the student.
FERPA applies to schools that receive funding under any program administered by the U.S. Department of Education. Private and faith-based schools at the elementary and secondary levels are generally not subject to FERPA.
Some of the most common FERPA violations include:
- Failing to implement adequate data security programs.
- Denying an eligible student or parent access to the student’s records.
- Including protected student information on a mailing list or shared documents.
Additionally, the explosion in the use of digital technologies has transformed how things are done at schools since FERPA was originally passed. Social media usage, remote learning and online applications and registrations are among security factors that must be considered. The ability to follow FERPA regulations also may be hindered by an increase in cyberattacks, which means being vigilant in preventing threats, choosing only reputable vendors and teaching stakeholders how to protect themselves is essential.
Recent FERPA Updates Address Security Concerns
Modern technology and methods of communication have drastically increased the need for cybersecurity. This is especially important for universities and colleges, where students frequently utilize social media, study or work remotely and regularly communicate with one another and instructors online.
The most recent updates to the FERPA occurred on May 24, 2024, and earlier in 2023. Updates primarily focused on modernizing the regulations to address current technological advancements and the evolving educational environment.
Key changes include:
- Enhanced Data Sharing for Research: The new regulations permit educational institutions to disclose PII without consent for studies or audits of educational programs, provided there are strict privacy safeguards in place. This includes mandatory written agreements with organizations conducting such studies to ensure the protection of student data, as stated on the National Law Review website.
The updates clarify that student health records may be considered education records under FERPA, but “treatment records” of eligible students are excluded from this definition and therefore not protected by FERPA.
The regulations also provide institutions with detailed, required provisions aimed at preventing PII from ending up in the hands of persons or entities not intended or permitted to receive them, as well as guidelines for addressing data breaches.
- Increased Use of Technology: The amendments explicitly include students who receive instruction through online or cyber schools under the definition of “attendance.” This ensures that FERPA’s protections extend to students in virtual learning environments.
These updates aim to balance the need for data privacy with the practicalities of modern education, ensuring that student information remains protected while allowing for necessary administrative and educational functions.
Cybersecurity and Data Protection in Schools
With increased technology use and students completing their work or communicating remotely, schools are experiencing an increase in cyberattacks.
As noted on the Arctic Wolf website, Verizon’s 2024 Data Breach Investigations Report shows that the educational services sector experienced 1,780 incidents in 2023, with 1,537 of them involving confirmed data disclosure. This represents a 258 percent year-over-year increase in the number of incidents and a 545 percent increase in the amount of data disclosure. Overall, approximately 900 U.S. schools were impacted.
The reasons why schools seem to be targeted include the belief that a social engineering attack is more likely to be successful, along with the fact that the data includes plenty of information about individuals’ health, demographic and financial information.
Arctic Wolf and several other organizations have noted the following examples of cyberattacks that occurred in U.S. schools over the past several years. Afterward, each of these schools implemented additional strategies and systems to further protect their data.
- According to various posts online, cybercriminals forging a ransomware attack were successful in extorting $1.14 million out of a leading medical-research institution at a university in California that was working on a cure for COVID-19 in June 2020. The school paid in order to recover its own data.
- A ransomware attack at a university in Washington, D.C., in September 2021 forced the university to shut down its campus Wi-Fi and cancel remote classes for several days.
- A December 2020 ransomware attack at a university in California affected 300 organizations. The hackers exploited a vulnerability in third-party software to insert ransomware and extract personal data from government agencies, businesses and educational institutions, including this university. In late March 2021, the perpetrators used the stolen data to engage in mass mailings and the posting of data online to blackmail individuals and companies into giving them money.
- A NetWalker ransomware attack targeted Michigan State University in May 2020. The perpetrator(s) threatened to release private information if they did not receive an undisclosed ransom amount. Impacted servers and workstations were quickly taken offline, and the university refused to pay. In response to the attack, the university centralized IT resources and instituted additional protections, including supporting VPNs via the university’s central IT department, employing multi-factor authentication and restricting user access.
Higher education institutions are not the only schools to be targeted, as K-12 schools are often attacked as well.
In fact, from 2018 to 2021, K-12 schools in most states reported cyber incidents on their systems, and reported incidents had risen from 400 in 2018 to over 1,300 in 2021, according to the Department of Education.
According to Arctic Wolf and a story posted on the Associated Press website, the computer system of one of the nation’s largest school districts, the Broward County Public Schools in Florida, was hacked by a criminal gang that encrypted district data. The hackers demanded $40 million in ransom and, if they did not receive it, threatened to erase the files and post students’ and employees’ personal information online. The ransomware attack exposed the personal information of approximately 50,000 students and employees, including names, dates of birth, Social Security numbers and healthcare-related information.
In another example, the Los Angeles Unified School District – the second-largest district in the country – disclosed that approximately 2,000 assessment records of current and former students were posted on the dark web as a result of a cyberattack in February 2023. The posted records included an unspecified number of driver’s license numbers and Social Security numbers, according to a post on the Los Angeles Times website.
.jpg)
Third-Party Vendors
All of these factors combined lead to questions about whether marketing professionals can use student lists, as well as how third-party vendors can protect sensitive data.
Data collected by K12 Security Information Exchange shows that 55 percent of all data breaches at K-12 schools between 2016 and 2021 were carried out on schools’ vendors. In 2022, for example, a ransomware attack on a single website hosting services vendor took down the websites of 5,000 schools across the country. According to a post on the TechCrunch website, school districts in Kansas City, Illinois and Missouri were impacted. The incident prevented some schools from sending email notifications about school closures due to COVID-19 outbreaks.
Marketing to higher education students requires a balance between protecting families’ sensitive data and helping educational institutions attract audiences or promote special events.
According to FERPA regulations, K-12 and higher education institutions may create student directories, but students may opt out of them. However, schools are not obligated to allow a student to take a class anonymously, such as for higher education online classes.
FERPA permits schools to outsource institutional services or functions that involve the disclosure of education records to contractors, consultants, volunteers or other third parties as long as the outside party:
- Performs a service for which the agency or institution would otherwise use employees.
- Is under the direct control of the agency or institution with respect to the use and maintenance of education records.
- Is subject to the requirements that the PII from education records may be used only for the purposes for which the disclosure was made.
- Meets the criteria specified in the school or local educational agency’s annual notification of FERPA rights for being a school official with a legitimate educational interest in the education records.
Schools should make it a practice to enter into a written agreement with any external organizations prior to sharing any PII from education records, according to the Department of Education.
Law enforcement records that pertain to students are not “education records” subject to the privacy protections of FERPA. However, PII from education records that schools share with a law enforcement unit do not lose their protected status.
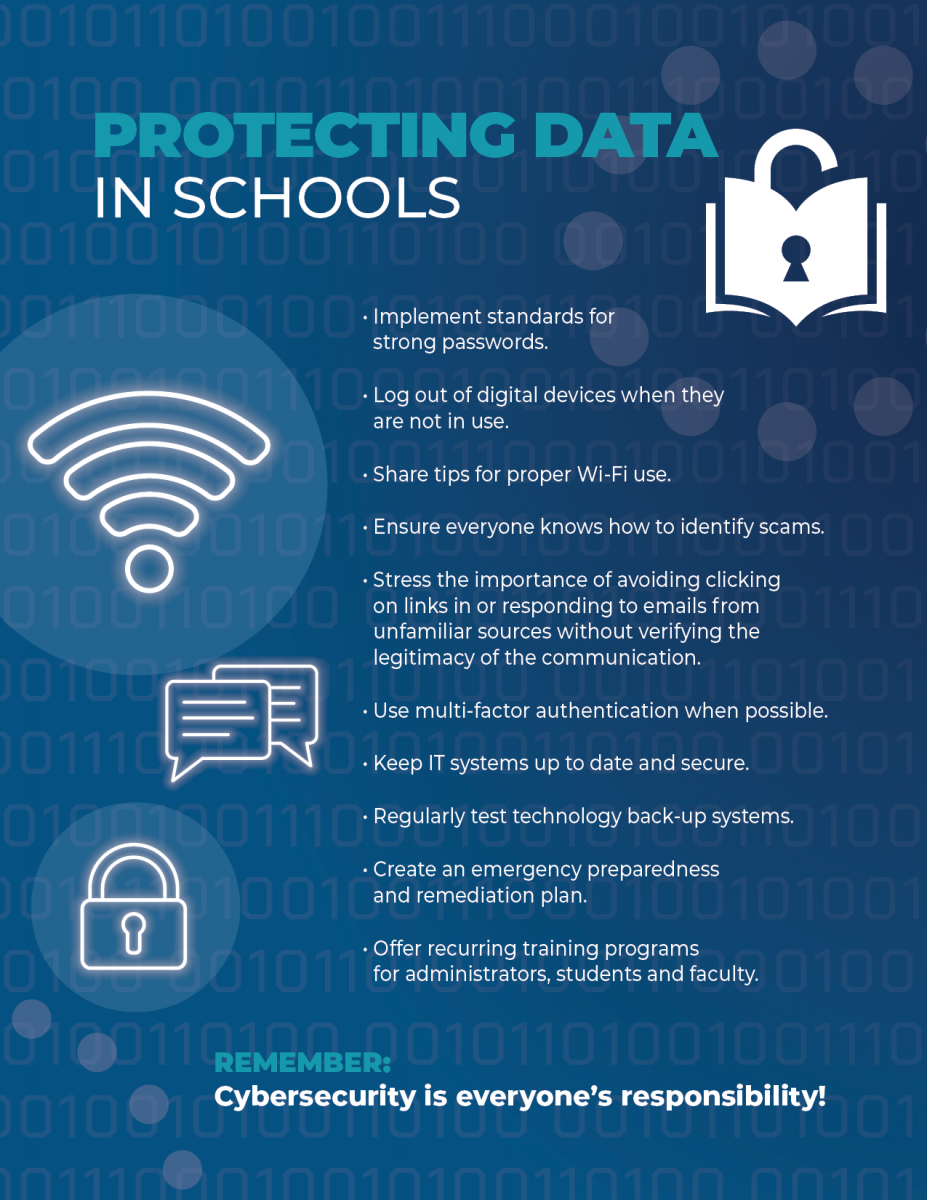
How Educational Institutions Can Stay Protected from Cyber Attacks
Higher education institutions can take many steps to help protect their students’ data. Instituting and following cybersecurity frameworks can help ensure compliance with the FERPA regulations. These frameworks include:
- The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF)
- The Center for Internet Security (CIS) Critical Security Controls Framework
- The International Organization for Standardization 27001 (ISO 27001)
- The ISACA (formerly the Information Systems Audit and Control Association) Control Objectives for Information and Related Technologies (COBIT)
The following safeguards can also help protect schools and universities from cyberattacks, as well as minimize the potential for FERPA violations:
- Reduce risks by reinforcing the fact that security is everyone’s responsibility.
- Implement standards for strong passwords, including discouraging the sharing of passwords and requiring all students, faculty and administrators to change their passwords every few months.
- Teach all stakeholders tips for proper use of Wi-Fi and how to avoid falling prey to phishing or other types of online scams.
- Set up multi-factor authentication whenever possible.
- Ensure that IT teams keep systems as up to date as possible, as new scams are created every day — and with Artificial Intelligence factored into the equation, scams are trickier than ever.
- Create an emergency preparedness plan that outlines the steps your school will take in the event of a breach. Among other factors, the plan should include:
- Prevention protocols.
- How to quickly access your response team in the event of a breach. The team should include your school’s top administrators, the IT staff, a human resources representative and public relations personnel
- Steps for immediate correction, including identifying the source of the breach, shutting down systems if necessary and securing any data that may be compromised.
- How to create a remediation plan after the incident based on the newfound information you may have encountered. Fix any vulnerabilities.
- A communication plan to address questions from stakeholders, the public and the media, as well as how to contact your legal team if necessary.
Higher Education Marketing
Implementing and following stringent security protocols is essential to keeping students’ data secure, as well as ensuring compliance with FERPA regulations.
Colleges and universities must attract students in order to move forward, and they may work with higher education marketing solutions providers to help them meet their goals. However, it’s of utmost importance to work with a marketing organization that understands FERPA policies and places every priority on protecting data.
For more information about Phoenix Innovate’s transformative and sustainable solutions for higher education marketing, see our website or contact us online. Phoenix Innovate maintains HITRUST certification, which outlines the highest standards of data security, as well as omnichannel marketing strategies, innovative technologies and direct and digital marketing to help colleges and universities meet their goals.
